We recently received an industrial x-ray machine for use in the Eclypsium office make the next doctor manhattan Do serious cyber security research. Among the X-rays of yet-to-be-released industrial IT technologies, from giant companies whose names we cannot reveal, we have conducted some other fun experiments.

The only thing we’ve done with it so far was to x-ray some FTDI USB to UART cables. We had an old cable lying around which was looking a bit suspicious and useless. It worked at slow speeds but it failed when transferring firmware images from a product. These failures prompted us to purchase a known good cable from DigiKey, which worked as expected. It’s possible that this older cable came from a factory that also produced older generations of authentic FTDI cables, but this particular chip did not meet the performance requirements for the FTDI brand. Or perhaps it was a production run based on stolen FTDI IP. Or it is actually completely unrelated to any FTDI IC but is programmed in software to claim to be FTDI. Until we can accurately match the silicon to a known supply chain, we can really only guess.
In any case, we wanted to see the difference between the questionable cable and a newer, more apparently “legitimate” cable, which cost about $20 from DigiKey. It is not a stretch to assume that a suspicious looking cable is a fake. FTDI has publicly announced issues with counterfeit devices. He has also fought drivers who sell counterfeit chips. Some people have also called it vendor-sanctioned malware.
Here’s what both cables look like to the naked eye:


Take a look at the two X-ray images below and see if you can tell which one is suspicious and which one is authentic. Then scroll down and we’ll tell you what we see.
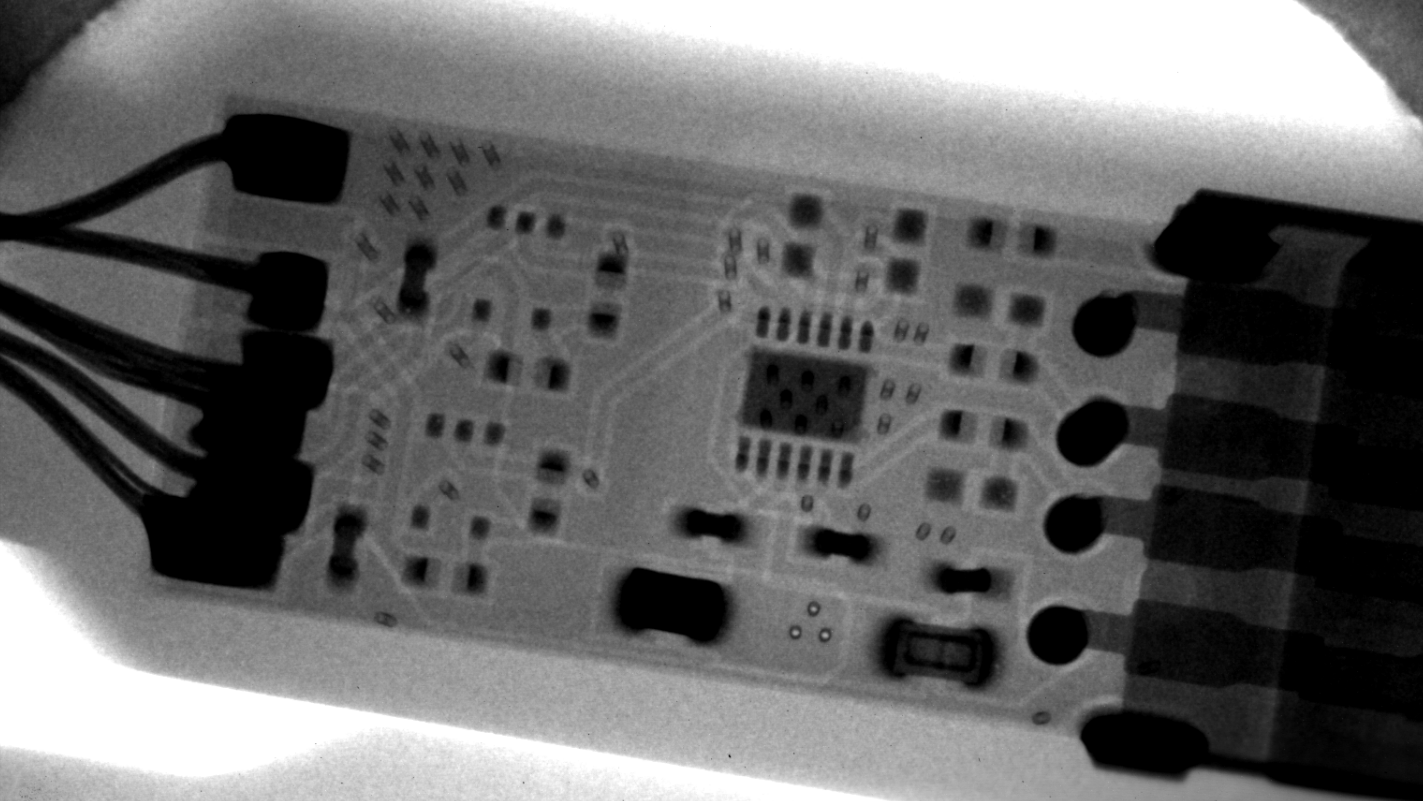

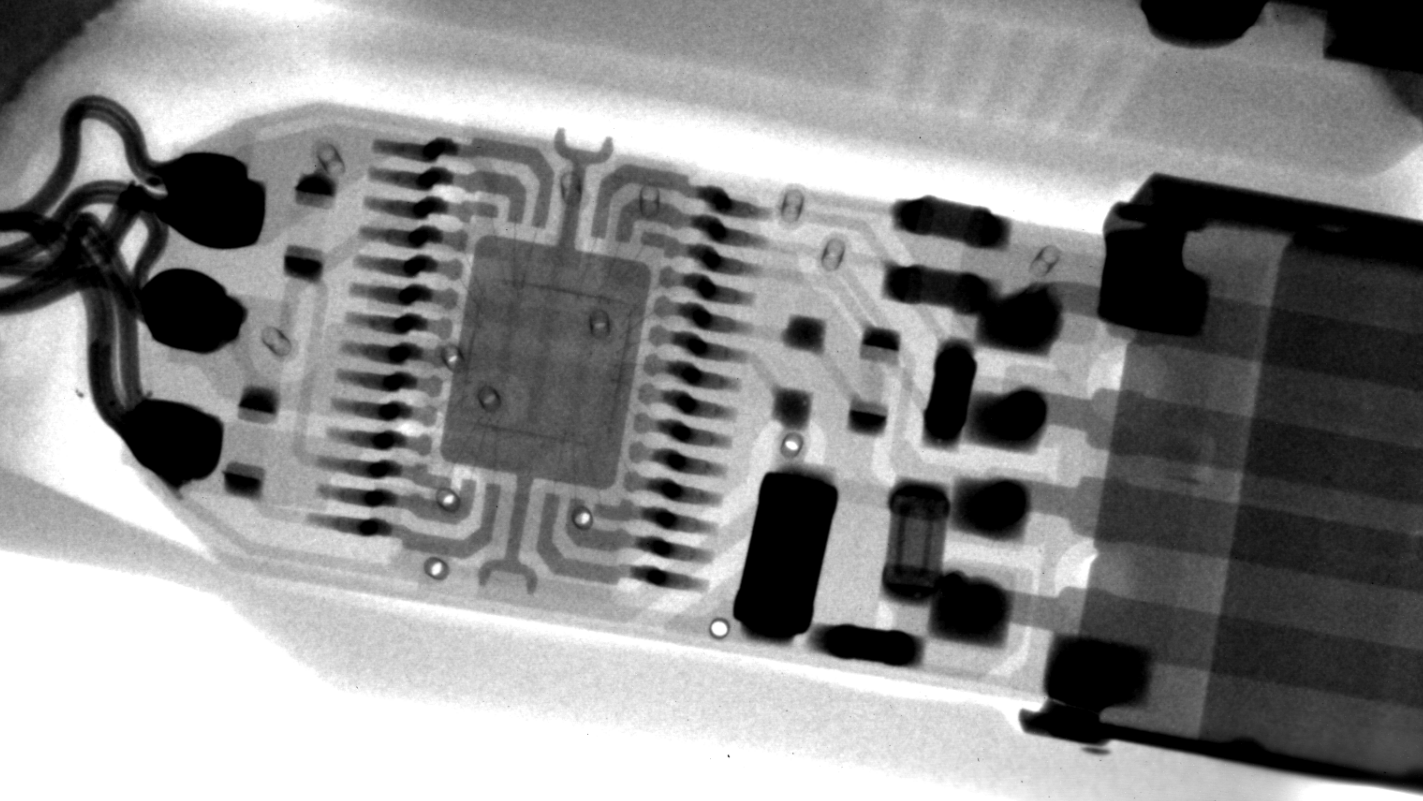

Before we tell you the answer, here are some clues to look for in each picture. Authentic cable has the following characteristics visible in an X-ray image, which are not shared with suspect cable:
- Inserting ground (reduces impedance and ground loops while improving EMI resistance and thermal dissipation). Although there is some debate about the actual value of copper ground pours, they are still used by reputable manufacturers.
- ground stapling
- Decoupling passives near the main integrated circuit (IC)
- More isolation passive for USB data pins
- thermal pad under ic
- Engineered strain relief for wire connections
- More solder for the mechanical tabs on the USB A connector
- Younger/Newer Silicon Process
- better passive alignment
The big reveal, and implications for supply chain security
Okay, the top image above is the authentic cable. The image below is more questionable.
Did you get it right? If not, go back and see if you can figure out different clues.
The point is, even if you know what to look for, it’s not easy to spot a fake. The consequences probably won’t be too bad for a consumer purchasing a questionable USB cable. But what happens when an enterprise gets counterfeit network gear with a backdoor already installed? Or when a major bank acquires gray market servers containing data from another company? Eclypsium has helped major organizations around the world address these types of supply chain problems.
Supply chain risks are increasing rapidly. As AI data center projects capture more and more of the global supply of chips, memory, storage and other key resources, the secondary market for all of these is heating up. The speed and complexity of these supply chains leaves vulnerabilities that cyber adversaries can exploit to introduce vulnerable components and backdoors into technology that make their way into critical infrastructure.
To learn more, check out our white paper on why supply chain security demands a focus on hardware
<a href
